Explore the top 4 authentication mechanisms for secure access.
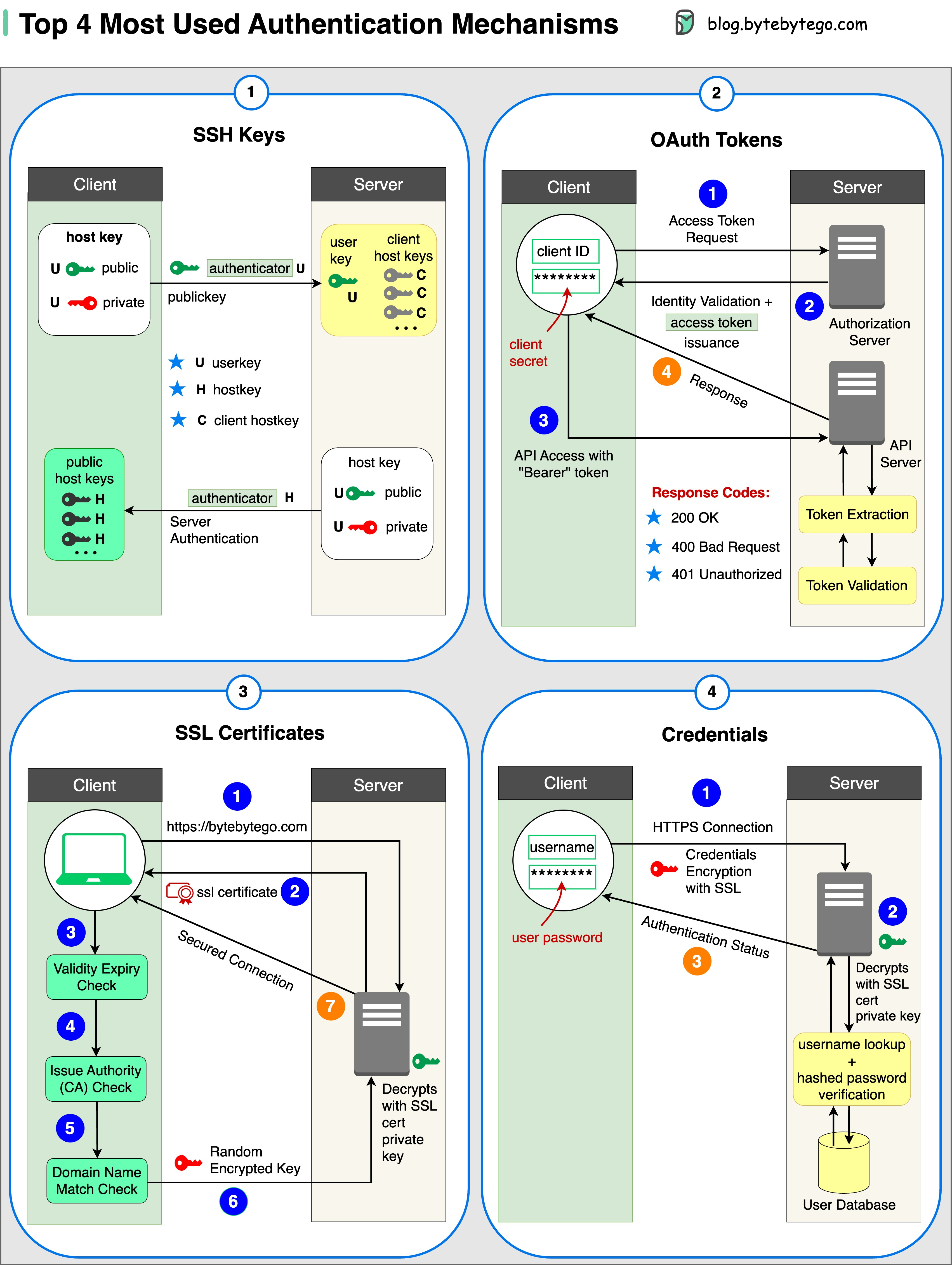
Cryptographic keys are used to access remote systems and servers securely.
Tokens that provide limited access to user data on third-party applications.
Digital certificates ensure secure and encrypted communication between servers and clients.
User authentication information is used to verify and grant access to various systems and services.
Over to you: How do you manage those security keys? Is it a good idea to put them in a GitHub repository?
Guest post by Govardhana Miriyala Kannaiah.